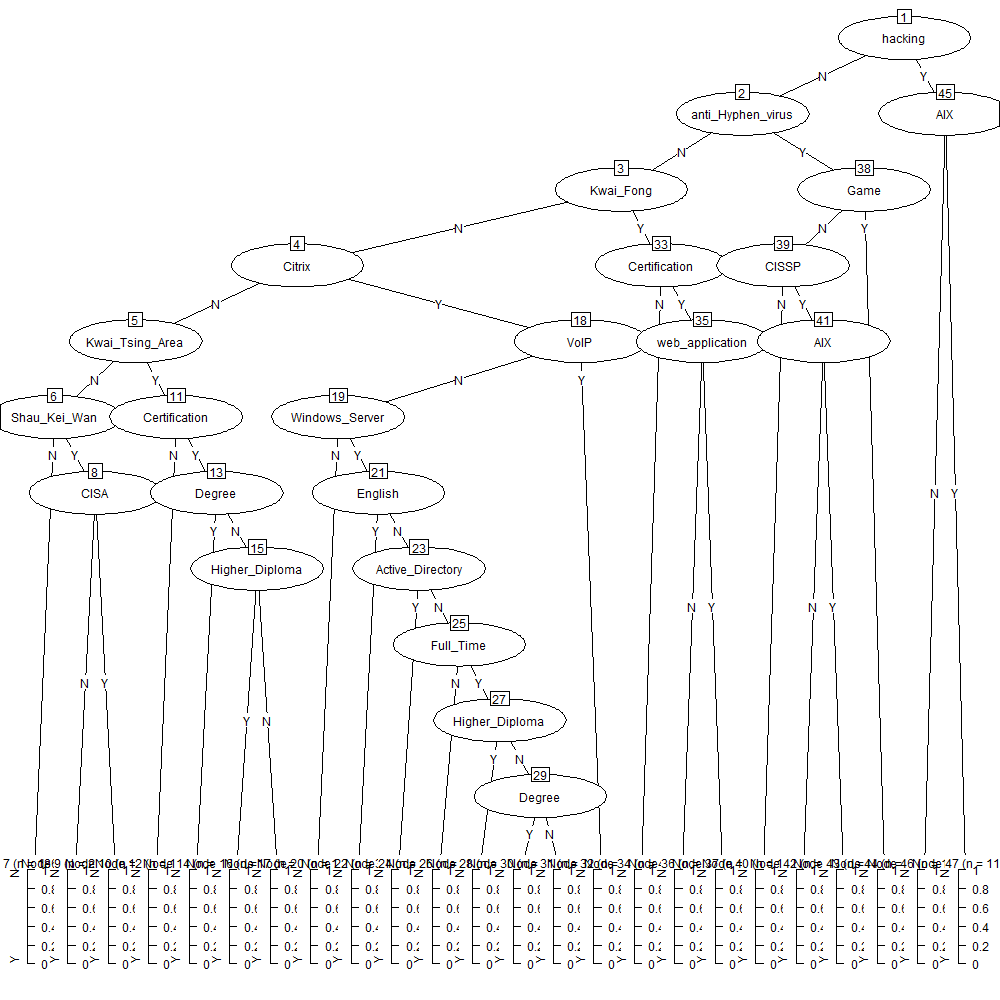

[1] root
| [2] hacking in N
| | [3] anti_Hyphen_virus in N
| | | [4] Kwai_Fong in N
| | | | [5] Citrix in N
| | | | | [6] Kwai_Tsing_Area in N
| | | | | | [7] Shau_Kei_Wan in N: N (n = 186353, err = 0.0%)
| | | | | | [8] Shau_Kei_Wan in Y
| | | | | | | [9] CISA in N: N (n = 257, err = 0.0%)
| | | | | | | [10] CISA in Y: Y (n = 9, err = 22.2%)
| | | | | [11] Kwai_Tsing_Area in Y
| | | | | | [12] Certification in N: N (n = 1889, err = 0.1%)
| | | | | | [13] Certification in Y
| | | | | | | [14] Degree in Y: N (n = 47, err = 0.0%)
| | | | | | | [15] Degree in N
| | | | | | | | [16] Higher_Diploma in Y: N (n = 9, err = 0.0%)
| | | | | | | | [17] Higher_Diploma in N: Y (n = 21, err = 4.8%)
| | | | [18] Citrix in Y
| | | | | [19] VoIP in N
| | | | | | [20] Windows_Server in N: N (n = 1616, err = 0.1%)
| | | | | | [21] Windows_Server in Y
| | | | | | | [22] English in Y: N (n = 322, err = 0.0%)
| | | | | | | [23] English in N
| | | | | | | | [24] Active_Directory in Y: N (n = 84, err = 0.0%)
| | | | | | | | [25] Active_Directory in N
| | | | | | | | | [26] Full_Time in N: N (n = 44, err = 0.0%)
| | | | | | | | | [27] Full_Time in Y
| | | | | | | | | | [28] Higher_Diploma in Y: N (n = 11, err = 0.0%)
| | | | | | | | | | [29] Higher_Diploma in N
| | | | | | | | | | | [30] Degree in Y: N (n = 12, err = 8.3%)
| | | | | | | | | | | [31] Degree in N: Y (n = 21, err = 9.5%)
| | | | | [32] VoIP in Y: N (n = 13, err = 30.8%)
| | | [33] Kwai_Fong in Y
| | | | [34] Certification in N: N (n = 449, err = 0.0%)
| | | | [35] Certification in Y
| | | | | [36] web_application in N: N (n = 12, err = 41.7%)
| | | | | [37] web_application in Y: Y (n = 9, err = 0.0%)
| | [38] anti_Hyphen_virus in Y
| | | [39] Game in N
| | | | [40] CISSP in N: N (n = 1001, err = 1.1%)
| | | | [41] CISSP in Y
| | | | | [42] AIX in N: N (n = 19, err = 31.6%)
| | | | | [43] AIX in Y: Y (n = 8, err = 0.0%)
| | | [44] Game in Y: Y (n = 13, err = 15.4%)
| [45] hacking in Y
| | [46] AIX in N: N (n = 127, err = 1.6%)
| | [47] AIX in Y: Y (n = 11, err = 0.0%)
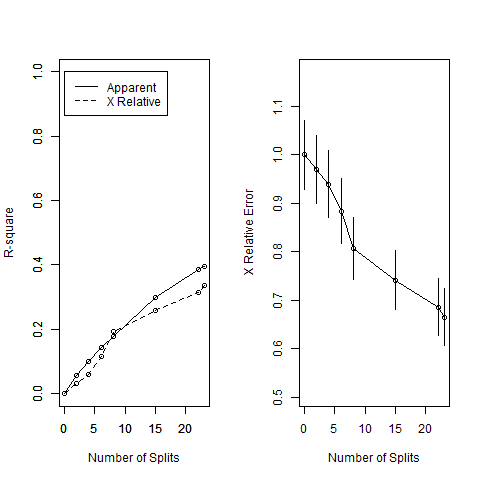
Number of inner nodes: 23
Number of terminal nodes: 24
Created by Mr. Cyrus Wong, Data Scientist.
For update, please join the IVE - Information Technology Facebook page.
For technical explanation, please join the Report Facebook page.
For discussion, please join my facebook group or linkedin me.
Sponsored by:
supported by AWS in Education Grant award